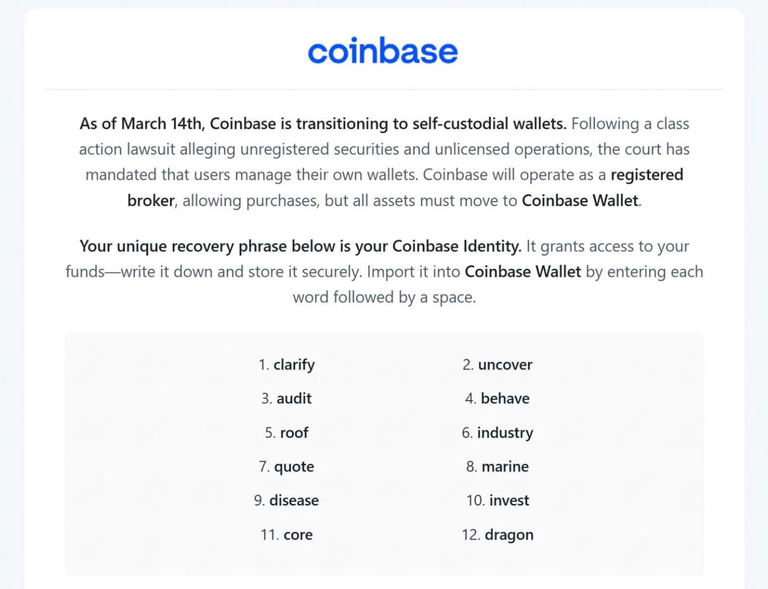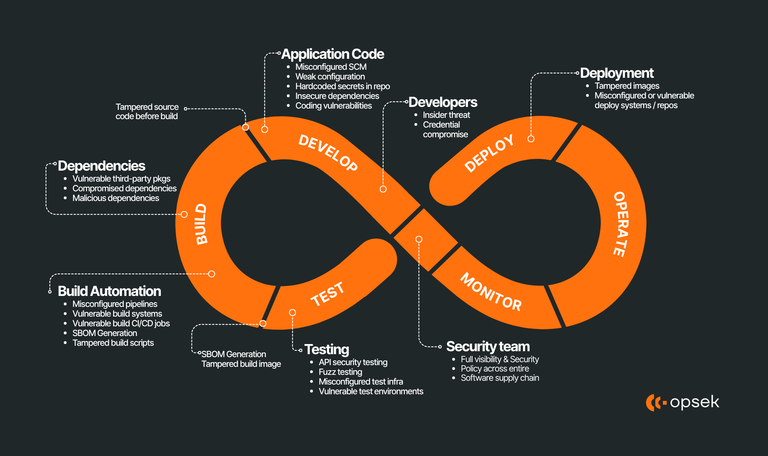
Code is law, but the supply chain is the lawmaker
How the software supply chain actually works in modern development? Software development today is layered: your code depends on libraries, those libraries depend on others, your CI system pulls everything automatically, and the final bundle gets shipped to users. In this structure, the “supply chain” in software is not about physical parts, but about the chain of trust in software artifacts, source, builds, and distribution. In crypto ecosystems, where user