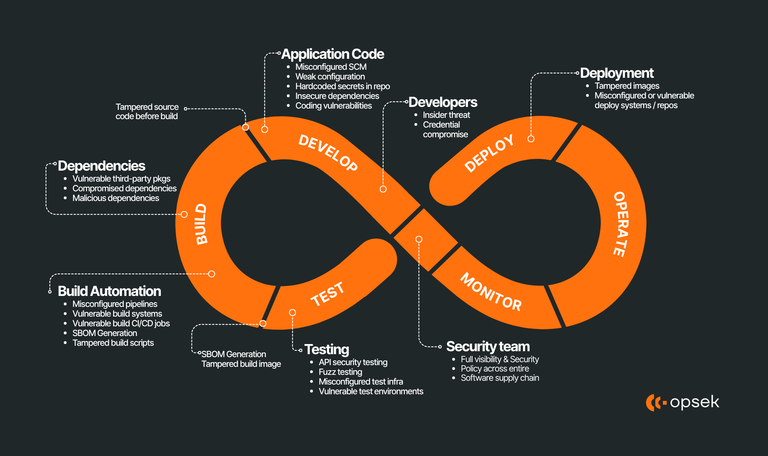
THE OPSEC WAKEUP CALL
A recap and takeaways of some stuff we talked about some days ago during the "Don't Get Rekt" episode 4 "THE OPSEC WAKEUP CALL" by RektHQ with @officer_secret: DPRK, Operational security, physical security and kidnappings, Bybit, hardware wallets, and more. Current status of web3 security: 99% of stolen funds are not due to smart contract hacks anymore, but Operational security issues, this means